RTCP - Uwu?
Posted on sam. 25 janvier 2020 in CTF
solves : 401
Point : 125
ᵘʷᵘ oh no ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ hecc sorry guys ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ sorry im dropping ᵘʷᵘ my uwus all over the ᵘʷᵘ place ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ oh no I lost one ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ ᵘʷᵘ
ah, Jake, you idiot
Hint: https://riceteacatpanda.wtf/uwu
Hint 2: This challenge gets progressively harder the faster your internet is if you do it manually
We got the visit the link and got a bunch of redirections (5 in total). It's coming from a HTML redirect : <meta http-equiv="Refresh" content="0; url=/omgmeow" />.
- https://riceteacatpanda.wtf/uwu
- https://riceteacatpanda.wtf/omgmeow
- https://riceteacatpanda.wtf/pandaaaaaaa
- https://riceteacatpanda.wtf/you-better-wash-your-rice
- https://riceteacatpanda.wtf/footprint
- https://riceteacatpanda.wtf/uwustorage
We have different ways to do it.
From the web browser
We can use the developper tools inside the web browser to log all requests make. For each requests, we can look inside the response and check with CTRL+F if the content contains the flag.
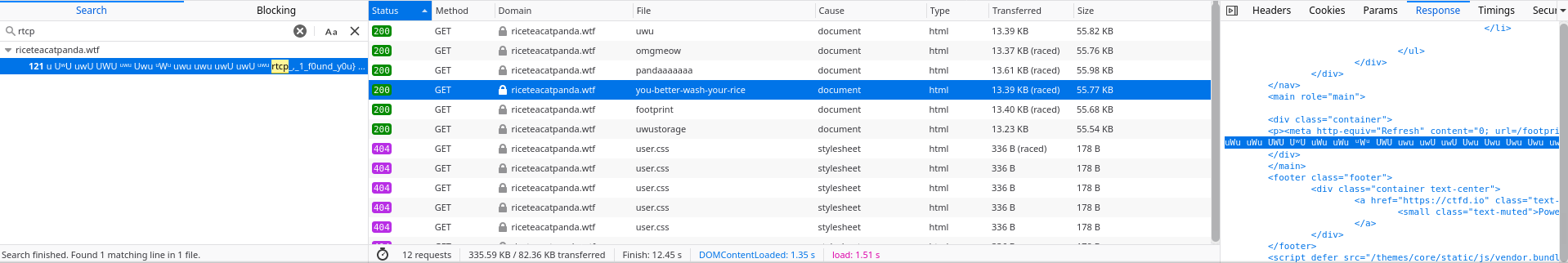
CLI
We can url each page to check if the flag is inside and get the next page to check.
$ curl -s https://riceteacatpanda.wtf/uwu | grep -i rtcp
$ curl -s https://riceteacatpanda.wtf/uwu | grep -i Refresh
<p><meta http-equiv="Refresh" content="0; url=/omgmeow" />
$ curl -s https://riceteacatpanda.wtf/omgmeow | grep -i rtcp
$ curl -s https://riceteacatpanda.wtf/omgmeow | grep -i Refresh
<p><meta http-equiv="Refresh" content="0; url=/pandaaaaaaa" />
$ curl -s https://riceteacatpanda.wtf/pandaaaaaaa | grep -i rtcp
$ curl -s https://riceteacatpanda.wtf/pandaaaaaaa | grep -i Refresh
<p><meta http-equiv="Refresh" content="0; url=/you-better-wash-your-rice" />
$ curl -s https://riceteacatpanda.wtf/you-better-wash-your-rice | grep -i rtcp
uWu uWu UWU UʷU uWu[...]rtcp{uwu_,_1_f0und_y0u}[...]UʷU uWu ᵘWᵘ</p>
BURP
to-do