Pragyan 2020 - Encuéntralo si puedes
Posted on mer. 26 février 2020 in CTF
Encuéntralo si puedes (350pts)
Solved by: 12%
Luis is very fond of music. Recently he developed a keen interest in CTF challenges. He makes a challenge for yankee and asks him if he could break it and find the code from it. Help yankee to find the secret code.
The flag format - p_ctf{OBTAINED_SECRET_CODE}
$ ffprobe despacito_luisFonsi.mp3
[...]
Input #0, mp3, from 'despacito_luisFonsi.mp3':
Metadata:
track : 01
Software : Lavf58.33.100
artist : Luis Fonsi ft. Daddy Yankee
genre : POP
Unknown text information frame: 2017
title : Despacito
comment : Better go last than first
album : Despacito
date : 2017
Duration: 00:05:21.43, start: 0.023021, bitrate: 166 kb/s
Stream #0:0: Audio: mp3, 48000 Hz, stereo, fltp, 166 kb/s
Metadata:
encoder : LAME3.100
Ok, we know how to look for the information: end of the song.
We can use Audacity to open the file and use the spectogram view to show the information:
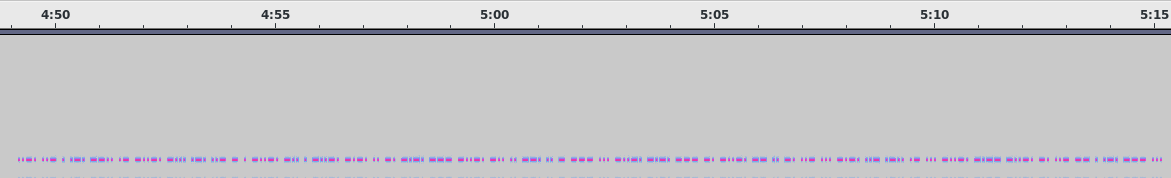
Looks like morse code. After right all down, we can decode and got a message:
..-. ..- . .-. –.. .- -..-. -... .-. ..- – . -..-. -.. . -..-. -.-. .. -. -.-. — -..-. -.. .. –. .. – — ... -..-. -.-. — -. -..-. — .. -. ..- ... -.-. ..- .-.. .- ... -..-. -.– -..-. -. ..- — . .-. — ...
FUERZA/BRUTE/DE/CINCO/DIGITOS/CON/MINUSCULAS/Y/NUMEROS
We know now what kind of password we are looking. The tool pdfcrack can be use with specify the the minimal/maximal (-n and -m) lenght and space of the password (-c).
$ ./pdfcrack -f ../1Hola.pdf -c "abcdefghifklmnopqrstuvwxyz0123456789" -n 5 -m 5
PDF version 1.3
Security Handler: Standard
V: 2
R: 3
P: -3904
Length: 128
Encrypted Metadata: True
FileID: 34ef3f1f94c5a1a642014ddf22af7900
U: 5233de370d2758db5857a2a21592631c00000000000000000000000000000000
O: fc81cb565ad34c0f8d431ec8772e44d7ee7da867715f50294bfe5b23116564c4
Average Speed: 28059.7 w/s. Current Word: 'zabma'
[...]
Average Speed: 27737.7 w/s. Current Word: 'v3dmz'
Average Speed: 28639.5 w/s. Current Word: 'p2nyz'
found user-password: 'x2n1z'
Ok, we got the first password for the PDF files. Let's do the same for the two others files: found user-password: '39adz' and found user-password: '8yfa2'.
We got the two PDFs used to explain the SHA1 collision: https://shattered.io/. The last PDF told us how to get the flag: SHA1[original files] = base64-decrypt(base64-decrypt(flag)).
So, download the orignal file, and compute the base64 encode twice to it:
$ echo "p_ctf{$(echo -n $(printf "$(sha1sum shattered-1.pdf | sed 's/^\([^ \t\s[:space:]]\+\).*$/\1/')" | base64) | base64)}"
p_ctf{TXpnM05qSmpaamRtTlRVNU16UmlNelJrTVRjNVlXVTJZVFJqT0RCallXUmpZMkppTjJZd1lRPT0=}`.